It's well known that NSA and also maybe others have already broken encryption algorithms in many applications. idk about Signal tho.
Privacy
A community for Lemmy users interested in privacy
Rules:
- Be civil
- No spam posting
- Keep posts on-topic
- No trolling
Yeah no, the NSA isn't capable of breaking modern encryption.
Trust leads to the dark side
Fine, go verify it
Sadly, Im not qualified to do that. It’s still my messenger of choice.
Then not to be aggressive about it, but go get qualified or stop spreading FUD honestly...
Cant server isnt foss they could be doing anything with metadata.
It is, but open source servers never matter anyways
I thought it was open source.
https://github.com/signalapp/Signal-Server
This doesn't prevent them from running different software or logging requests, but we have unsealed court orders, which is better than most other services that could receive them.
Sorry ur right. But yeah as u said they could be running anything. Im confident in the fact they cant read messages just not so confident they arent collecting metadata capable of building a social graph. Sealed sender doesnt do much good when u have a centralised server.
The server is Foss. However, that means nothing as you still be using it. Best to not trust it and use ee2e which is what Signal does.
Signal is really a fancy version of SMS and MMS. It does require a phone number but contacts don't need that you contact you. There are better options from a anonymity perspective but they aren't as user friendly and popular.
I convinced my non-tech nerd partner to switch to Matrix and it’s been working suprisingly well for us.
Is that (non)-(tech nerd) or (non-tech) (nerd) partner?
she’s not a tech nerd
Aha, thanks, just wondering. English isn't my first language.
Imo, I think Signal is a good "normie-oriented secure messenger", but I think Simplex is more worthy of focus.
Agreed. The thing with Signal is that it has a longer history and a lower barrier to entry.
The only one I trust is Briar.
Not a bad choice. Briar has usability limitations but in terms of democracy it is a powerful tool.
I'd also recommend taking a look at Threema.
I think their product direction is a bit better. Particularly as Signal still shows a message that they don't back sync messages before you paired devices "for your security" ... Threema also doesn't back sync messages in their beta multi device setup, but that seems to be more less of a product stance and more of a "we just don't do it yet."
Threema is definitely missing some features like emoji reactions, stories, and a builtin cryptocurrency (which depending on your stances might be pros or cons).
Both apps have definitely gotten better over the years; I think Threema's multi device support has really drained resources on their side so there hasn't been as much outward feature work. I'm hoping it won't be terribly long until that changes.
Why would they need crypto dawg
IMO, they wouldn't
While it isn't necessarily an argument against Threema's security, I think it's important to consider that Threema is owned by a privately held company ^[1[2]]^ — Signal is owned by a non profit ^[3]^.
References
- "Threema". Threema GmbH. Accessed: 2024-12-09T02:40Z. https://threema.ch/en/secure-messenger.

- "GmbH". Wikipedia. Published: 2024-09-27T06:24Z. Accessed: 2024-12-09T02:44Z. https://en.wikipedia.org/wiki/GmbH.
- "Signal Foundation". Signal Foundation. Accessed: 2024-12-09T02:45Z. https://signalfoundation.org/.
Signal Foundation formed in 2018 to support Signal Messenger which originated in 2012. Through the Foundation, we have been able to support Signal's growth and ongoing operations as well as investigate the future of private communication.
I almost think that's a pro. I don't understand how signal intends to pay for servers forever with voluntary donations. Though I'd be fine if they set up a mandatory annual fee.
Signal is far more polished IMO but both are great.
I almost think that’s a pro. I don’t understand how signal intends to pay for servers forever with voluntary donations.
In the same vein, a privately owned service, to me, is rather suspect if it is free of cost — the money's gotta come from somewhere.
Threema sells to businesses. It's a one time fee for personal.
It’s a one time fee for personal.
Ah, so there is! ^[1][2[3]]^ I didn't notice that. Thank you for pointing out that inconsistency in my previous comment; what I stated was conjecture, and, lo and behold, it turned out to be wrong.
References
- "Threema. The Secure Messenger". "Threema GmbH". Google Play. Google. Published: 2024-11-27Z. Accessed: 2024-12-11T02:45Z. https://play.google.com/store/apps/details?id=ch.threema.app.
- "How do I install Threema Libre?". Threema. Accessed: 2024-12-11T02:49Z. https://threema.ch/en/faq/libre_installation.
- ¶1.
Threema Libre is available exclusively via F-Droid. It requires a Threema Shop license, and the F-Droid app needs to be installed on your Android device.
- ¶1.
- "Buy Threema for Android". Threema. Accessed: 2024-12-11T02:52Z. https://shop.threema.ch/en/buy.
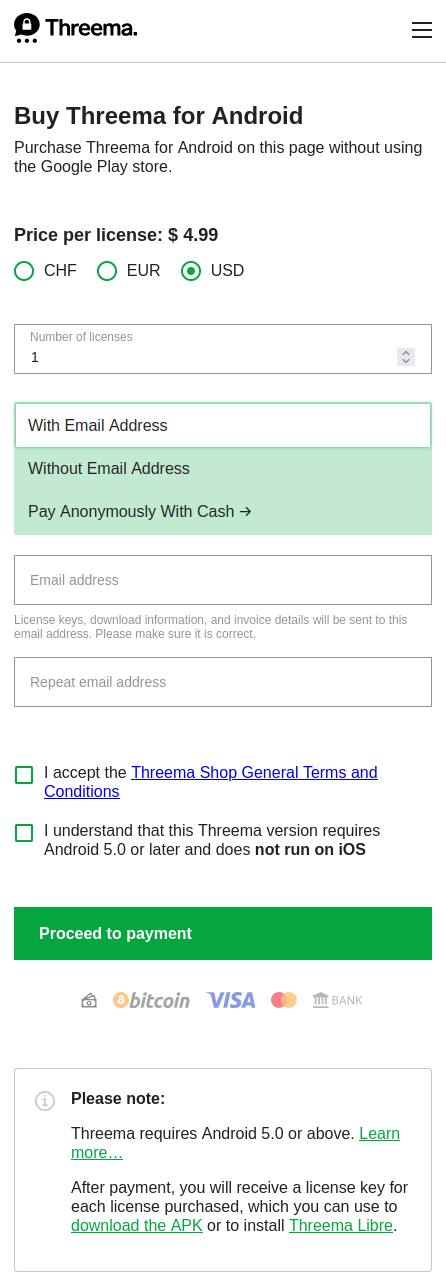
I don’t understand how signal intends to pay for servers forever with voluntary donations.
I think donations can be sustainable if the service in question is handled correctly. Imo, federation/decentralization would improve this, as it wouldn't place the cost burden on a single entity.
If you're seriously concerned about privacy and security I wouldn't look at Threema. They severely mishandled vulnerabilities by insulting the security researchers, then introduced a new protocol they built with the advice given to them for free from the SAME researchers before that, and yet it still doesn't support critical features like full forward secrecy. If all you want primarily is the best security out there Signal is and will be the best for a long time to come by the looks of it.
I think that's a characterization of what happened but not necessarily a good representation of what actually happened.
Yes, some researchers in Zurich found vulnerabilities. Yes they down played them ... because you still couldn't read anything. They were also already working on a new protocol before those researches wrote their paper and yes I'm sure they made some tweaks based on their findings.
This is their response; I'd hardly call it "insulting" https://threema.ch/en/blog/posts/news-alleged-weaknesses-statement
You could say the same thing about Signal's response to their "desktop security scandal" earlier this year (of which Threema wasn't vulnerable and Signal repeatedly refused to acknowledge as a problem).
yet it still doesn't support critical features like full forward secrecy
They do support PFS (perfect forward secrecy) though their new multi-device solution doesn't yet support it.
https://threema.ch/en/blog/posts/ibex
This is the same protocol they were already working on when the "researches they insulted" released their research finding issues with the old protocol.
Threema is also far more active with third-party audits than any other group: https://threema.ch/en/faq/code_audit
They severely mishandled vulnerabilities by insulting the security researchers, then introduced a new protocol they built with the advice given to them for free from the SAME researchers before that, and yet it still doesn't support critical features like full forward secrecy.
IMO this entire sentence is just wrong.
As you said, if PFS can be disabled by enabling a feature on the receiving end it's by security practices not enabled, in the industry that's called a downgrade attack and considered very bad practice.
The blog post you linked, is the publicly revised version after they were called out by well known cryptographers for their handling. This was their original response to the researchers, again after the researchers disclosed the vulnerabilities to them and actively helped designing the new protocol, not just giving inspiration. This was their initial tweet: „There’s a new paper on Threema’s old communication protocol. Apparently, today’s academia forces researchers and even students to hopelessly oversell their findings“ which is long deleted, but I did read it while it was still up back then. I can't find a screenshot or anything at the moment, so if you want to call me a liar, go ahead but if you search for that quote you will find many citations.
Also, they claimed „old protocol“ but Ibex was still months from being deployed widespread, so that's another big downplay.
You mention Signals Desktop app issue, Threema claimed the attacks were unrealistic because they require significant computing power or social engineering, both things that are definitely a risk if you're trying to protect yourself from bigger intelligence efforts. The issue with Signal Desktop however, required full file system access to your device at which point, there is nothing stopping the attacker from simply using a key logger, capturing your screen, etc.
This is why no big security researchers called out Signal but many shunned Threema. At the end I don't have a horse in the race for either of them, but I think those are facts people need when making a decision with their private information.
As you said, if PFS can be disabled by enabling a feature on the receiving end it's by security practices not enabled, in the industry that's called a downgrade attack and considered very bad practice.
I don't have an iOS device to know for sure but I'm fairly certain they inform you and participants in your chats about the PFS interruptions. It's a temporary problem you have to deal with to use a beta application.
One of their devs was on mastodon talking about how PFS was more complicated with their design than they expected because they need to sync up the devices. Signal took the approach of sending one message to every device and Threema sends it to one of your devices and then that device sends it to the others. From what I understand this makes the PFS session key synchronization harder for Threema so it's not implemented yet.
This was their initial tweet: „There’s a new paper on Threema’s old communication protocol. Apparently, today’s academia forces researchers and even students to hopelessly oversell their findings“
The issue with Signal Desktop however, required full file system access to your device at which point, there is nothing stopping the attacker from simply using a key logger, capturing your screen, etc.
Right but in practical terms many of the findings cited against Threema were equally if not more doubtful. I don't know who the "big security researchers" you're referencing are, but ... as someone in the tech sector myself I do tend to agree that we've gotten to a place of really happenstance exploits being sold as if they're like the old zero days where the user doesn't have to do anything, it works 100% of the time, and the user loses control of their system.
If that quote is real ... I think they were probably just miffed that the researchers didn't discuss the fact that they were already in the later design stages of protocol improvements and made their findings sound far more plausible to exploit than they were.
There's just a double standard here too... Threema gets shit for downplaying an exploit where you literally have to have physical access to the device, but it's totally fine that signal didn't even use basic operating system functionality (the keychain) to protect data at rest -- that's a physical AND digital risk?
Perfect Forward Secrecy has been around since version 5.0 (as an opt in beta feature) and enabled by default since 5.1.
https://threema.ch/en/blog/posts/security-proof-ibex
Here is the original statement you're referring to:
https://threema.ch/en/blog/posts/news-alleged-weaknesses-statement
I don't see any insults and the vulnerabilities were patched.
I agree that they downplayed it a bit, but back then they were still a for profit company. Now they are non-profit and it is in their interest to handle such cases in a way that is more aligned with their customers instead of their profits.
Simplex is the only one I would recommend out of those
-
Jami is based on a ancient broken codebase and it lacks a security audit
-
Session has several issues but most recently the screwed over the people who were silly enough to buy crypto.
-
I have never heard of Cwtch so that rules that out
I don't trust Signal. Haven't used it since it went down when people and capitol rioters fled WhatsApp and signed up. My understanding is it's a brittle centralized system just like WhatsApp.
AND back when I did use it, the app had dark patterns that included spamming all your contacts when you set up the app.
Matrix still needs work, but it is the future in this space.
Matrix still needs work, but it is the future in this space.
Matrix can send encrypted events ^[1.1]^, but, imo, the Matrix protocol is a firehose of metadata ^[1.3][1.2]^. I'd argue that metadata leakage doesn't lend itself well to anonymity; if one seeks anonymity, then I think they should seek to reduce their metadata footprint, as, logically, any information is better than no information when trying to identify someone.
References
- "Client-Server API". "Matrix Specification". Matrix Foundation. Version: 1.12. Accessed: 2024-12-09T02:21Z. https://spec.matrix.org/v1.12/client-server-api
- §"Sending encrypted attachments" (§10.12.1.7). https://spec.matrix.org/v1.12/client-server-api/#sending-encrypted-attachments.
- §"Extensions to
m.room.message msgtypes" (§10.12.1.7.1). https://spec.matrix.org/v1.12/client-server-api/#extensions-to-mroommessage-msgtypes. - §"Events" (§10.2.1). https://spec.matrix.org/v1.12/client-server-api/#events-2.
I think that's fair, maybe I should have said efforts like Matrix.
But I'd also view a singular commercial company's no-cost product as not being a long term bet on privacy/anonymity.
But I’d also view a singular commercial company’s no-cost product as not being a long term bet on privacy/anonymity.
Oh I completely agree with the idea that a federated service, like Matrix ^[1]^, is far preferable to a centralized one, eg Discord ^[2]^; I have no issue with using Matrix (I personally use it extensively) I just think one should be careful with the idea of using it with the intent of being anonymous.
References
- "Matrix Specification". Matrix Foundation. Version: 1.12. Accessed: 2024-12-09T06:41Z. https://spec.matrix.org/latest/.
Matrix defines a set of open APIs for decentralised communication, suitable for securely publishing, persisting and subscribing to data over a global open federation of servers with no single point of control. […]
- "Discord". Wikipedia. Published: 2024-12-07T05:34Z. Accessed: 2024-12-09T07:03Z. https://en.wikipedia.org/wiki/Discord#Features.
-
- The license is listed as "proprietary". This was interpreted to mean that Discord is the owner of all of their infrastructure.
-
I don’t trust Signal. Haven’t used it since it went down when people and capitol rioters fled WhatsApp and signed up. My understanding is it’s a brittle centralized system just like WhatsApp.
Imo, there are more components to trust than service reliability (iiuc) — eg: trust in the underlying protocol, trust in the governing body etc.
Yes, I agree.
Is that an "agree" as in you hadn't considered what I said, or that you agree to that in addition? If it was the latter, I should clarify that I wasn't adding supplementary information — I was outlining what I thought was a flaw in your rationale (eg argument from ignorance) for distrust in Signal.
It's an agree as in I don't really feel like arguing with another user here. I don't buy the point about metadata when Signal, a centralized service like Discord (why are we talking about Discord?), may be able to scrape it too. Or the point about anonymity when Signal is far from the right tool for that purpose too, see above "spams your contact list."
For reliability, I'm not concerned with how much RAM Signal's servers have. What I should have highlighted is that Signal can nuke your communications on accident / on purpose / under coercion. And it's proven because they've already done it before. Mitigate that by having a backup system set up? That necessarily doubles your surface area for breaks in privacy or whatever a given user is worried about. So starting with Signal in the first place doesn't make sense to me.
For reliability, I’m not concerned with how much RAM Signal’s servers have. […]
I'm not sure that I understand this statement. What does RAM have to do with with Signal's infrastructure reliability?
[…] What I should have highlighted is that Signal can nuke your communications on accident / on purpose / under coercion. […]
Are you referring to the possibility that they may be able to block communications, as they are a centralized service?
[…] starting with Signal in the first place doesn’t make sense to me.
If you have the means to choose something more secure/trustworthy/robust than Signal, then I think it would be in your best interest to do so! I personally would recommend SimpleX, if possible.
[…] And it’s proven because they’ve already ["nuked" communications] before. […]
Would you mind providing a source of this? This sounds interesting, and good to know.
I don’t buy the point about metadata when Signal […] may be able to scrape it […]
I agree that it it within the realm of possibility, but, imo, this is independently verifiable, as the Signal apps are open-source ^[1][2][3]^ and offer reproducible builds (except iOS ^[2.1]^) ^[1.1][3.1]^. See this section on Signal's metadata for some more concrete information ^[4]^.
References
- "signalapp/Signal-Android". Github. Published: 2024-12-06T21:08:08.000Z. Accessed: 2024-12-11T05:38Z. https://github.com/signalapp/Signal-Android.
- Filepath: "reproducible-builds". Published: 2024-10-29T18:36:34.000Z. Accessed: 2024-12-11T05:40Z. https://github.com/signalapp/Signal-Android/tree/main/reproducible-builds.
- "signalapp/Signal-iOS". Github. Published: 2024-12-04T21:19:41.000Z. Accessed; 2024-12-11T05:41Z. https://github.com/signalapp/Signal-iOS.
- "Reproducible builds" (#641). Author: "Jeroen Massar" (massar). Issues. Published: 2015-03-03T09:16:05Z. Accessed: 2024-12-11T06:11Z. https://github.com/signalapp/Signal-iOS/issues/641.
- "signalapp/Signal-Desktop". Github. Published: 2024-12-04T22:57:07.000Z. Accessed: 2024-12-11T06:12Z. https://github.com/signalapp/Signal-Desktop.
- Filepath: "reproducible-builds". Published: 2024-11-21T03:14:21.000Z. Accessed: 2024-12-11T06:15Z. https://github.com/signalapp/Signal-Desktop/tree/main/reproducible-builds.
- "Signal Protocol". Wikipedia. Published: 2024-11-30T04:32. Accessed: 2024-12-11T06:18Z. https://en.wikipedia.org/wiki/Signal_Protocol#Metadata.
- §"Properties". §"Metadata".
Signal is encrypted but they still feed meta data to Alphabet boys
Make no mistake that it is part of the us security apparatus.
While for most it really doesn't matter, take note where we are heading in light of the recent adjustment to a affluent parasites life.
Who do you think the spooks will side during the first corpo war?
We just don't know but they will know who you keep in touch with...
How so?
Signal also uses our metadata encryption technology to protect intimate information about who is communicating with whom—we don’t know who is sending you messages, and we don’t have access to your address book or profile information. We believe that the inability to monetize encrypted data is one of the reasons that strong end-to-end encryption technology has not been widely deployed across the commercial tech industry.
Source: https://signal.org/blog/signal-is-expensive/
I haven't verified that claim investigating the source code, but I'm positive others have.