this post was submitted on 27 Sep 2023
42 points (100.0% liked)
Technology
37711 readers
163 users here now
A nice place to discuss rumors, happenings, innovations, and challenges in the technology sphere. We also welcome discussions on the intersections of technology and society. If it’s technological news or discussion of technology, it probably belongs here.
Remember the overriding ethos on Beehaw: Be(e) Nice. Each user you encounter here is a person, and should be treated with kindness (even if they’re wrong, or use a Linux distro you don’t like). Personal attacks will not be tolerated.
Subcommunities on Beehaw:
This community's icon was made by Aaron Schneider, under the CC-BY-NC-SA 4.0 license.
founded 2 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
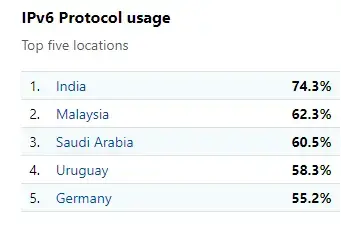
Governments should require IPv6 support for any online service or connected device they buy. If that's not a requirement for (sub)contractors, then they won't put effort into it.
This kind of requirements might also exclude a lot of crappy devices/services that have an outdated tech stack.
A common requirement in government contracts is "there must be no IPv6 support, and if there is it must be verifiably disabled to decrease the size of the vulnerability surface."
Many years ago, that misconfigured firewall that let IPv6 traffic through without even bothering to log it, resulting in a years-long compromise scared a lot of govvies, but unfortunately it taught them the wrong lesson.
Source: I'm a former Beltway Bandit.
The wrong lesson?
I'm not sure how reducing your attack surface area is the wrong lesson here.
The wrong lesson learned was, "don't use IPv6." Which has, to a large extent, hurt the uptake of IPv6 everywhere, because "if the government doesn't use it, we're not going to use it." Rather than do something sensible, like enable the IPv6 functionality of the firewalls and configure them properly.