this post was submitted on 09 Apr 2024
106 points (93.4% liked)
Privacy
31991 readers
514 users here now
A place to discuss privacy and freedom in the digital world.
Privacy has become a very important issue in modern society, with companies and governments constantly abusing their power, more and more people are waking up to the importance of digital privacy.
In this community everyone is welcome to post links and discuss topics related to privacy.
Some Rules
- Posting a link to a website containing tracking isn't great, if contents of the website are behind a paywall maybe copy them into the post
- Don't promote proprietary software
- Try to keep things on topic
- If you have a question, please try searching for previous discussions, maybe it has already been answered
- Reposts are fine, but should have at least a couple of weeks in between so that the post can reach a new audience
- Be nice :)
Related communities
Chat rooms
-
[Matrix/Element]Dead
much thanks to @gary_host_laptop for the logo design :)
founded 5 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
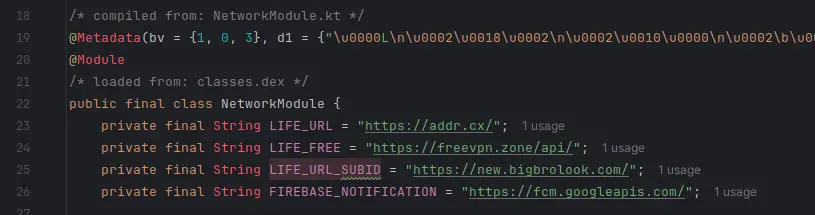
 Is used once here;
Is used once here;
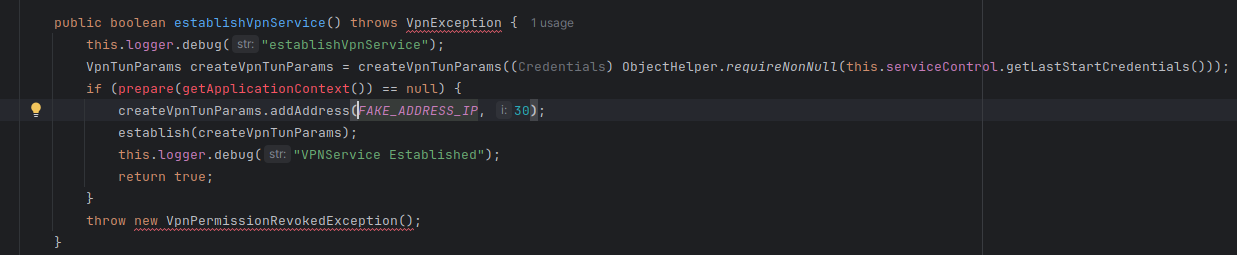
Probably not. It looks like it's setting the fake address before reading the tunnel parameters, where the real address is stored. Probably a kludge in case the connection address is undefined so the program doesn't crash. So check whether the address is included there.
Also check the function that establishes the connection. 10.1.1.1 is not a public subnet, so unless there is a VPN device listening at the local address, the tunnel should fail to establish and throw an error, triggering the exception clause in that code. Again, you'll want to confirm that in the code.
That seems to be the case, probably a killswitch-type feature, ensuring the VPN is working. Additionally, addr[.]cx is a free GeoIP lookup service, and I assume bigbrolook (OP - Big Brother is a term for a surveillance state, the porn definition is only used for 5-10 years) is/was another one. You can confirm with waybackmachine.
Seems to be an amateur free VPN using free infrastructure. Most of the time the free VPNs that turn their users machines into a proxy or do other dirty things will be obfuscated and require at least a bit of reverse engineering, not just opening a debugger and peeking.
Not trying to cast shade here, but isn't a master's thesis after you know a subject incredibly well, and aren't you supposed to look at things no one has looked at before? In case you're not in tech and this is a master's for another subject, this has been done.